Secure VPS Hosting: DDoS Protection, Firewall & Encryption Explained
- By Anis Ur Rahman
- 21 Feb, 2026
Looking for secure VPS Hosting that won't let attackers walk right in? This guide covers the security features that actually matter — and how to use them.
Your VPS is live, and traffic is coming in. Then — without warning — your server goes dark, no access, no response. That's a real-time DDoS attack. And the reality is, it occurs far more often than people expect.
In 2023, Cloudflare stopped a then-record 71M rps DDoS attack. Fast-forward to 2025: Q1 saw 20.5M attacks blocked (up 358% YoY), with SMBs—often on virtual servers—facing 70% of hyper-volumetric threats, per Cloudflare reports.
So, is VPS hosting actually secure? Can it be encrypted? What does firewall protection really mean in a VPS context? This guide answers all of it — clearly and without fluff.
Is VPS Hosting Secure?
Yes — but only when it's properly configured.
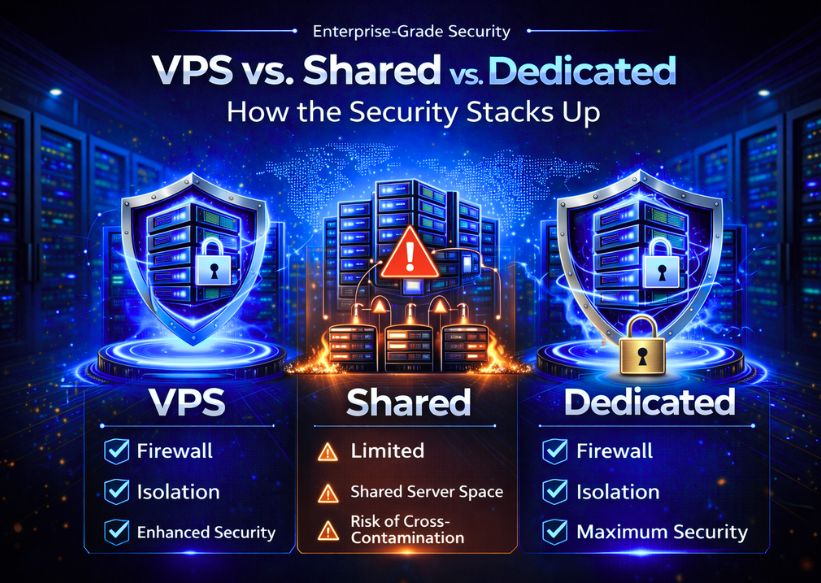
A Virtual Private Server gives you a dedicated slice of a physical machine. Unlike shared hosting, your files, memory, and CPU are isolated from every other user on that server. That isolation is the core security advantage of VPS hosting.
But isolation alone won't save you. You still need a working firewall, DDoS mitigation, encrypted connections, and strong access controls. Without those layers in place, even a well-isolated VPS is vulnerable.
Think of it like an apartment building. The building itself might have great security — cameras, a locked lobby, and a front desk but if you leave your own door unlocked, none of that matters.
What Is Virtual Isolation — And Why Does It Matter?
Virtual isolation means your VPS runs in its own sandboxed environment, completely separated from other users on the same physical hardware. This is made possible through hypervisor technology — software, such as KVM (Kernel-based Virtual Machine) or VMware, that creates and manages these isolated environments.
On shared hosting, a single compromised account can potentially expose every other account on the server. With a VPS, that risk disappears. Your resources are partitioned at the hardware level. What happens on another VPS cannot directly reach yours.
KVM-based VPS hosting — used by providers like Ummah Host BD, DigitalOcean, and Linode — delivers hardware-level isolation. That's the gold standard for anyone running security-sensitive workloads.
DDoS Protected VPS: What It Is and How It Works
A Distributed Denial-of-Service (DDoS) attack overwhelms your server by bombarding it with massive amounts of fake traffic. The objective is simple: overwhelm your bandwidth until your server collapses and legitimate users can't reach you.
Without protection, even a moderately sized attack can take your VPS offline for hours. With a DDoS-protected VPS, the host filters malicious traffic at the network edge — before it ever touches your server.
How to protect your VPS from DDoS attacks:
Choose a host with built-in DDoS mitigation — OVHcloud, Hetzner, and Vultr all include this by default
Put Cloudflare in front of your domain to absorb volumetric attacks at the DNS level
Enable rate limiting on your firewall to throttle suspicious traffic patterns
Install Fail2Ban to block IPs with repeated failed requests automatically
Monitor traffic in real time using Netdata or Datadog so you can respond fast
Read A Full Guide: High-Performance VPS Hosting in 2026
VPS with Firewall: Your First Line of Defense
A firewall determines which traffic is allowed to enter and exit your server. It's the most fundamental security tool you have — and most VPS users don't configure it properly.
Most Linux VPS instances come with UFW (Uncomplicated Firewall) pre-installed. It's the easiest starting point for beginners and covers most use cases.
How to set up a firewall on your VPS (UFW quick start):
Install UFW: `sudo apt install ufw`
Block all incoming traffic by default: `sudo ufw default deny incoming`
Allow outgoing traffic: `sudo ufw default allow outgoing`
Allow SSH access: `sudo ufw allow 22/tcp`
Allow web traffic: `sudo ufw allow 80` and `sudo ufw allow 443`
Enable the firewall: `sudo ufw enable`
Verify rules: `sudo ufw status verbose`
Critical warning: Always allow SSH before enabling the firewall. If you enable it first, you'll lock yourself out of your own server permanently.
Beyond the OS-level firewall, providers like DigitalOcean and Vultr offer cloud-level firewalls through their control panels. These sit above the operating system and block traffic before it even reaches your VPS. Use both — they complement each other.
Can a VPS Be Encrypted?
Absolutely. And you need to encrypt in two distinct places.
Encryption in transit protects data moving between your VPS and your users. Every VPS should have an SSL/TLS certificate installed. Let’s Encrypt issues free SSL/TLS certificates with built-in 90-day automatic renewal. This enables HTTPS and ensures all data in transit is unreadable to anyone intercepting it.
Encryption at rest safeguards all data saved on your server’s storage drive. Even if an attacker gets physical access to the hardware — or if a data center seizes your machine — encrypted storage is completely unreadable without the decryption key.
On Linux, this is handled by LUKS (Linux Unified Key Setup), which can encrypt your entire disk or specific partitions. Some managed VPS providers also offer encrypted volume options directly through their dashboard. The rule is simple: encryption in transit stops interception. Encryption at rest stops physical theft. You need both to be truly protected.
VPS Security Features: What to Look For
Not every VPS provider takes security equally seriously. Here's what separates a genuinely secure cloud VPS from a basic one:
Built-in DDoS mitigation — included by default, not sold as a premium add-on
KVM hypervisor — hardware-level isolation between VPS instances
Cloud-level firewall — sits at the network edge, above the OS
SSH key authentication support — no passwords, keys only
Two-factor authentication (2FA) — on the control panel and server login
Automated backups — fast recovery is a core part of security
Private networking — internal communication that never touches the public internet
SOC 2 / ISO 27001 certified data centers — independently verified physical and operational security
Learn Building Impenetrable Defenses: Attack Prevention Tips & Best Practices
VPS vs. Shared vs. Dedicated: How the Security Stacks Up
VPS hits the sweet spot — near-dedicated security at a fraction of the cost.
Which is Better for Bangladesh: Shared vs. VPS Hosting
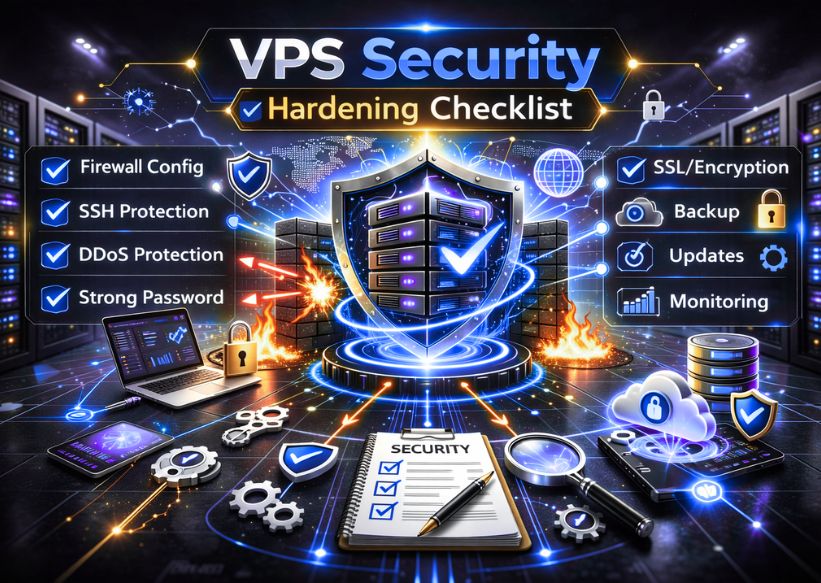
VPS Security Hardening Checklist
Run through this before you go live:
Disable root SSH login — create a non-root sudo user instead
Replace password authentication with SSH key pairs
Switch the default SSH port from 22 to a custom, non-standard port for added security.
Enable UFW with only the specific ports your application needs
Install Fail2Ban to block brute-force login attempts automatically
Turn on automatic security updates (`unattended-upgrades` on Ubuntu)
Install a free SSL certificate from Let's Encrypt for HTTPS
Enable LUKS disk encryption for any sensitive data workloads
Schedule automated backups — and test restoration regularly
Set up real-time monitoring with Netdata, Prometheus, or your host's built-in tools
Do these ten things consistently, and you're already more secure than the vast majority of VPS deployments out there.
Explore A Practical Guide: Choosing the Right BDIX VPS Plan
Frequently Asked Questions About secure VPS Hosting
Is VPS hosting secure?
Yes — significantly more secure than shared hosting. VPS isolation prevents other users on the same hardware from accessing your data. But you still need to configure a firewall, use SSH key authentication, encrypt your connections, and keep your system updated.
Are VPS servers secure against hacking?
A hardened VPS is much harder to compromise than shared hosting or an unprotected cloud instance. Disable unused services, restrict access, and stay current on patches. No server is completely hack-proof — but good hardening makes you a low-value target.
How do I protect my VPS from DDoS?
Choose a provider with built-in DDoS mitigation, use Cloudflare at the DNS level, configure Fail2Ban and rate limiting, and monitor traffic continuously.
Can a VPS be encrypted?
Yes. Use Let's Encrypt for in-transit encryption and LUKS for at-rest encryption. Some managed providers also offer encrypted storage volumes through their dashboard.
What is virtual isolation in VPS hosting?
It's the separation of your VPS from all other instances on the same physical server, enforced at the hypervisor level. If another user's VPS is compromised, yours remains completely unaffected.
What firewall should I use on a VPS?
UFW is the easiest option for most Linux setups. For more advanced control, use iptables or nftables directly. Combine your OS-level firewall with your provider's cloud-level firewall for maximum coverage.
Final Thought
Security isn't about being perfect. It's about making the attacker's job harder than it's worth.
Get your firewall configured and pick a host with DDoS mitigation built in. Encryption at rest protects the data saved on your server’s hard drive by keeping it encrypted. Use SSH keys — not passwords. Do those four things, and you've already closed the door on most threats.
The rest is staying consistent.
Explore a Complete Guide:
Global VPS Hosting Solutions – Scalable, High-Speed Servers Across the World

Author By
Anis Ur Rahman
Anis Ur Rahman writes domain and web hosting–related articles on behalf of Ummah Host BD. He works with domain name selection, web hosting, BDIX hosting, and website performance, and creates informational guides based on practical experience to help users make informed decisions. His writing focuses on providing reliable, easy-to-understand, and decision-supportive content.
Search Blog
Categories
Latest News

15 Feb, 2026
13 Feb, 2026